This involves two levels of encryption. The first is SIPS/TLS which is encryption of SIP signalling between the SARK PBX and your IP phone. It works in much the same way as HTTPS certificates do.
You can either purchase a certificate from a trusted source or generate your own self signed certificates. I’ll use self-signed certificates here because they are free and do the job for what I wanted.
The second part of encrypting your phone calls is the actual audio stream itself, the RTP. We can use SRTP, this is simply a case of turning it on but there’s no real point to doing this without firstly configuring SIPS/TLS because the keys used in SRTP encryption are passed in the SIP messages.
For me, there’s two reasons for doing all this.
The most obvious one is security, encrypting your phone calls means that anyone who is able to sniff your network traffic cannot extract your phone calls. For most people this is pretty unlikely but could happen all the same.
Perhaps of much more use is for remote or home workers and this is what made me get this working with SARK. One of the biggest problems in the world of VoIP is SIP-ALGs on routers making incorrect alterations to SIP packets. If your SIP packets are encrypted then any router they pass through cannot possibly make any alterations to them!
The steps to getting this working are (basically the same process on a SARK PBX as on any Asterisk PBX).
1) Generate self-signed certificates (commands issued at the Linux command prompt on SARK):
- cd /etc/asterisk
- mkdir ssl
- cd ssl
- echo 00 > file.srl
- openssl req -out ca.pem -new -x509 -days 365
- openssl genrsa -out server.key 2048
- openssl req -key server.key -new -out server.req -days 365
- openssl x509 -req -in server.req -CA ca.pem -CAkey privkey.pem -CAserial file.srl -out server.pem -days 365
2) Configure Asterisk:
Edit the file ‘sark_sip_header.conf’ either from the command line or in Asterisk File Edit in the SARK web interface. Add the following:
tlsenable=yes
tlsbindaddr=xx.xx.xx.xx
tlscafile=/etc/asterisk/ssl/ca.pem
tlsprivatekey=/etc/asterisk/ssl/server.key
tlscertfile=/etc/asterisk/ssl/server.pem
tlsclientmethod=tlsv1
tlscipher=ALL
tlsdontverifyserver=yes
Replacing xx.xx.xx.xx with your system’s own IP address. The last line isn’t essential for us but means if Asterisk is connecting as a client to a TLS server (so you’d need a SIP service provider who does TLS), whether to verify their certificate or not. If you do verify their certificate then they cannot be using self-signed certificates.
3) Configure extensions:
You can specify which extensions will use TLS & SRTP (and any you don’t, stay using unencrypted SIP & RTP).
In the SARK web interface, edit the extension and go to the “asterisk” tab. Add these lines:
transport=tls
port=5061
encryption=yes
This will turn on both TLS and SRTP for that single extension.
It’s important to note that once you’ve applied this, the phone MUST use it and trying to Register without encryption will now fail.
4) Configure the firewall:
By default SARK PBX only allow in SIP over UDP but TLS uses TCP. You need to add a rule in the ‘firewall’ section of the SARK web interface to allow TCP port 5061 (SIPS/TLS uses 5061 by default). Note, you don’t need to allow RTP over TCP, SRTP still uses UDP normally.
5) Configure the phones:
This assumes you already have a phone configured and working using normal SIP, this is how to convert them to use SIPS/TLS & SRTP.
Snom phones (note, you’ll probably need a fairly recent firmware version)
- In identity #, add an outbound proxy such as “sip.mydomain.com:5061;transport=tls”. Where sip.mydomain.com is your SARK PBX’s hostname or IP address. You could also set up the correct DNS-SRV records for this (hint, _sips._tcp) but I’ll not go in to that here.
- In the RTP tab, turn on RTP Encryption, set SRTP Auth-tag to AES-80 and RTP/SAVP to Mandatory
Then when making or receiving a call, look out for the little “lock” symbol on the phone screen to signify SIPS/TLS & SRTP are both in use in the call in progress.
Yealink phones (I used v72 firmware, older may work too)
- In Account #, Register tab, set Transport to TLS, set Server Host Port to 5061.
- In the Advanced tab, set RTP Encryption(SRTP) to ‘Compulsory’
Much like Snom, the phone will also display a “lock” symbol on the screen during a call with SIPS/TLS & SRTP in use.
One last thing to note, both Snom and Yealink phones do not verify server certificates by default. This means that there is no protection against a man-in-the-middle attack (someone else pretending to be your SIP server). You can turn on certificate verification on either phone but you MUST also do one of the following in order for SIPS/TLS to continue to work:
- Purchase a certificate from a trusted source, much like you would if setting up a HTTPS website. Please speak to us first so we can advise you on the best place to buy as the phones have a limited number of CAs built into them in comparison to a web browser.
- Continue with your self-signed certificate but load the CA it was signed against into the phone. This is the “ca.pem” file generated earlier on. It is safe to distribute this to your phones, it cannot be used to be generate more certificates without the key (which you need to keep safe).
Any questions to paul@provu.co.uk



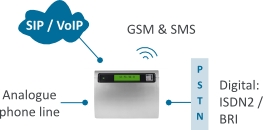 Wouldn’t it be nice if you turned up to install an IP PBX and all you had to do was connect the lines and phones and everything just worked, with inbound calls automatically routed to the connected phones. With the combination of a SARK phone system plus snom and Yealink IP phones, it can be this simple.
Wouldn’t it be nice if you turned up to install an IP PBX and all you had to do was connect the lines and phones and everything just worked, with inbound calls automatically routed to the connected phones. With the combination of a SARK phone system plus snom and Yealink IP phones, it can be this simple.